Transmission Control Protocol & Internet Protocol (TCP/IP)
The standard form of data transmission.
NETWORKING
1/8/20252 min read
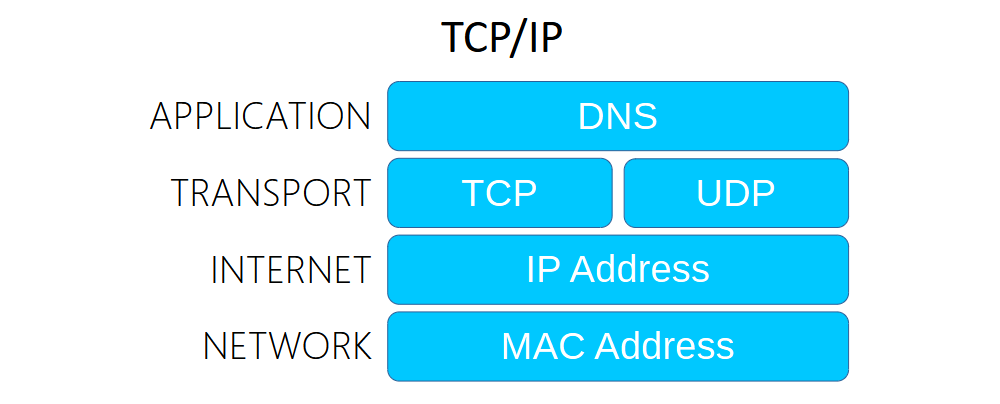
TCP/IP is the standard model for accurately and correctly transmitting data between two devices on the internet. TCP allows for data transmission while IP finds the destination of the device for the data to be sent. The data is assembled and then split into packets before being sent out in a particular order. Once the packets are received they are reassembled in the reverse order at their destination. This would be as if a puzzle was sent from one address in separate pieces by mail to the same receiving address. The TCP/IP model is divided into four layers;
4. Application - responsible to maintaining a connection for data exchange between the user and application (protocols: HTTP, FTP, POP3, SMTP, DNS, DHCP, SNMP)
3. Transport - builds and provides the entry and exit tunnel therefore a destination for efficient data transmission and manages traffic patterns, speeds and errors along with disassembling and reassembling packets (TCP/UDP)
2. Internet/Network - a function of the IP portion that controls and defines where packets are sent between devices. Transport layer protocols are not recognized here.
1. Physical/Network Access - the objects that physically make up a network this includes drivers and device MAC addresses.
The transfer of data occurs in a 3-step handshake process.
Establish a connection from the client to the server.
Establish a connection from the server to the client. A server could even be a computer.
Allow for the data to be communicated in both directions at the same time.
Although it was not previously mentioned the User Datagram Protocol or UDP is another protocol used in the transport layer in the TCP/IP stack. As opposed to TCP which is a stateful or connection-based protocol UDP is not. It is worth noting that data sent through this method is not encrypted and therefore vulnerable. One solution if in a browser setting is to enable DoH (DNS over HTTPS). This feature enhances privacy and security by encrypting DNS queries and responses. By doing so man-in-the-middle attacks such as packet sniffing, spoofing and cache poisoning attacks are more difficult to accomplish. DoH also blends in with regular HTTPS traffic in a kind of a gray man camouflage.
Ports:
TCP - 53 [DNS Tieback]
HTTP - 80
HTTPS/DoH - 443
Secure Shell - 22
SMB (Secure Message Block) - 445
RDP (Remote Desktop Protocol) - 3389
UDP - 53 [DNS Tieback]
Dynamic Host Configuration Protocol (DHCP) - 67 (server) / 68 (client)
Trivial File Transfer Protocol - 69 (not the be confused with FTP)
Network Time Protocol - 123
Let's Get Social
Be in the know by following IPv100
© 2026. IPv100 Inc.
